Notes while trying Wireguard VPN on some of my testbeds.
Following exactly instruction at https://www.wireguard.com/install/ to install Wireguard on server and clients.
Use 192.168.128.0/24 for VPN subnet as an example. The VPN Server is 192.168.128.254, and the VPN clients are from 192.168.128.1 - 253.
On RHEL 7.7
This is the Wireguard VPN server. I did not have any issues with installing and configuring the server.
Create wg-setup.sh shell script file just in case I need to setup again.
#!/usr/bin/env bash yum update -y # reboot # unless there were no updates sudo curl -Lo /etc/yum.repos.d/wireguard.repo https://copr.fedorainfracloud.org/coprs/jdoss/wireguard/repo/epel-7/jdoss-wireguard-epel-7.repo sudo yum install -y epel-release sudo yum install -y wireguard-dkms wireguard-tools
Again, create wg-server-config.sh shell script file in case I have to re-setup.
#!/usr/bin/env bash VPNSUBNET=192.168.128 VPNSERVER_IP=254 UDP_PORT=51820 # Create /etc/wireguard directory [ -d /etc/wireguard ] || sudo mkdir -p /etc/wireguard cd /etc/wireguard sudo umask 077 # Generate private/public key pair [ -f /etc/wireguard/privatekey ] || wg genkey | sudo tee /etc/wireguard/privatekey | wg pubkey | sudo tee /etc/wireguard/publickey # Create /etc/wireguard/wg0.conf file cat << EOF | sudo tee -a /etc/wireguard/wg0.conf [Interface] Address = $VPNSUBNET.$VPNSERVER_IP/32 PrivateKey = $(sudo cat /etc/wireguard/privatekey) ListenPort = $UDP_PORT # Add peers/clients below # [Peer] # PublicKey = # AllowedIPs = $VPNSUBNET.0/24 EOF
Create wg-server-addpeer.sh shell script file to add peers/clients later on.
#!/usr/bin/env bash VPNNET_ID=192.168.128 read "Enter (paste) your peer's public key here: " PEER_PUBLICKEY echo "Your peer's public key is: " $PEER_PUBLICKEY read "Enter last octet of client IP Address (Range: 1 - 254): " VPNHOST_ID # Append new peer's public key to /etc/wireguard/wg0.conf file on server cat << EOF | sudo tee -a /etc/wireguard/wg0.conf [Peer] PublicKey = $PEER_PUBLICKEY AllowedIPs = $VPNNET_ID.$VPNHOST_ID/32 # PresharedKey = EOF echo "REMEMBER to run: 'wg addconf wg0 <(wg-quick strip wg0)' to update server!"
On Fedora Workstation 30
Not any issue with this client.
On CentOS 7.7 Core
I had issue when getting the wg0 interface up.
[tuyendq@1 ~]$ sudo wg-quick up wg0 Warning: `/etc/wireguard/wg0.conf' is world accessible [#] ip link add wg0 type wireguard RTNETLINK answers: Operation not supported Unable to access interface: Protocol not supported [#] ip link delete dev wg0 Cannot find device "wg0" [tuyendq@1 ~]$
Solved: Remove wireguard-dkms and wireguard-tools packages, then reinstall those two packages.
On Debian 9 (Stretch)
Again, I had issue when getting the wg0 interface up.
tuyendq@3:~$ sudo wg-quick up wg0 [#] ip link add wg0 type wireguard RTNETLINK answers: Operation not supported Unable to access interface: Protocol not supported [#] ip link delete dev wg0 Cannot find device "wg0" tuyendq@3:~$ sudo modprobe wireguard modprobe: FATAL: Module wireguard not found in directory /lib/modules/4.9.0-9-amd64 tuyendq@3:~$
Solved: Run 'sudo apt upgrade'.
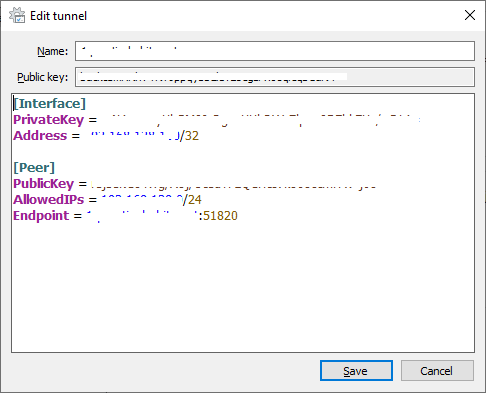
Wireguard client on Windows 10
Manually add tunnel
[Interface] PrivateKey = auto-generated-private-key-by-wireguard Address = your-client-assigned-ip-address/32 [Peer] PublicKey = wireguard-server-public-key AllowedIPs = your-vpn-subnet/24 Endpoint = wireguard-server-hostname-or-ip-address:51820
Upgrade wireguard using winget on Windows
PS C:\Users\tuyen> winget upgrade wireguard Found WireGuard [WireGuard.WireGuard] Version 0.5.3 This application is licensed to you by its owner. Microsoft is not responsible for, nor does it grant any licenses to, third-party packages. Successfully verified installer hash Starting package install... Successfully installed PS C:\Users\tuyen>
Wireguard client on Android
Wireguard client on Fedora IoT 31 on ARM-based Raspberry Pi 2
Fedora IoT 31
[tuyendq@p21 ~]$ hostnamectl
Static hostname: p21
Icon name: computer
Machine ID: 80f0038ac35e41ea97a3f04299159299
Boot ID: 39bc9979499946ac868c3d55dc27f31b
Operating System: Fedora 31 (Thirty One)
CPE OS Name: cpe:/o:fedoraproject:fedora:31
Kernel: Linux 5.3.7-301.fc31.armv7hl
Architecture: arm
[tuyendq@p21 ~]$
I could not install wireguard packages from jdoss/wireguard, as shown below.
[tuyendq@p21 ~]$ sudo dnf copr enable -y jdoss/wireguard [sudo] password for tuyendq: Repository successfully enabled. [tuyendq@p21 ~]$ sudo dnf install -y wireguard-dkms wireguard-tools Copr repo for wireguard owned by jdoss 253 B/s | 341 B 00:01 Failed to download metadata for repo 'copr:copr.fedorainfracloud.org:jdoss:wireguard' Fedora Modular 31 - armhfp 5.4 kB/s | 5.1 kB 00:00 Fedora Modular 31 - armhfp - Updates 7.0 kB/s | 6.2 kB 00:00 Fedora 31 - armhfp - Updates 6.2 kB/s | 6.1 kB 00:00 Fedora 31 - armhfp 5.4 kB/s | 5.2 kB 00:00 Ignoring repositories: copr:copr.fedorainfracloud.org:jdoss:wireguard No match for argument: wireguard-dkms No match for argument: wireguard-tools Error: Unable to find a match: wireguard-dkms wireguard-tools [tuyendq@p21 ~]$
Based on Adrian Mihalko's detailed instructions at Install WireGuard on Raspberry Pi 1, 2 (not v1.2), Zero, Zero W: "On these RPi's you need to compile manually. Why? The Raspberry Pi's CPU doesn't have some of the features of the armhf arch in Debian, if you download and install the armhf package, it will crash (Segmentation fault)."
So, try installing Wireguard from source. However, there are some modification for Fedora IoT 31: raspberrypi-kernel-headers -> kernel-headers, libmnl-dev -> libmnl-devel, libelf-dev -> elfutils-libelf-devel, build-essential -> @development-tools.
Install prerequite packages
$ sudo dnf install -y kernel-devel kernel-headers libmnl-devel elfutils-libelf-devel @development-tools
Make sure versions of running linux kernel and linux headers match.
[tuyendq@p21 src]$ uname -r 5.3.7-301.fc31.armv7hl [tuyendq@p21 src]$ ls /usr/src/kernels/ 5.3.8-300.fc31.armv7hl [tuyendq@p21 src]$
In my case, those versions do not match. So I run 'sudo dnf upgrade -y' to bring up linux kernel's version matching with linux headers' version. Must reboot and re-check those version.
[tuyendq@p21 ~]$ uname -r 5.3.8-300.fc31.armv7hl [tuyendq@p21 ~]$ ls /usr/src/kernels/ 5.3.8-300.fc31.armv7hl [tuyendq@p21 ~]$
It's good to move on.
$ git clone https://git.zx2c4.com/WireGuard $ cd WireGuard/src $ make $ sudo make install
Configure client and start interface
[tuyendq@p21 ~]$ sudo systemctl start wg-quick@wg0
[tuyendq@p21 ~]$ sudo systemctl status wg-quick@wg0
● wg-quick@wg0.service - WireGuard via wg-quick(8) for wg0
Loaded: loaded (/usr/lib/systemd/system/wg-quick@.service; disabled; vendor >
Active: active (exited) since Sat 2019-11-09 04:22:07 EST; 5s ago
Docs: man:wg-quick(8)
man:wg(8)
https://www.wireguard.com/
https://www.wireguard.com/quickstart/
https://git.zx2c4.com/WireGuard/about/src/tools/man/wg-quick.8
https://git.zx2c4.com/WireGuard/about/src/tools/man/wg.8
Process: 799 ExecStart=/usr/bin/wg-quick up wg0 (code=exited, status=0/SUCCES>
Main PID: 799 (code=exited, status=0/SUCCESS)
CPU: 343ms
Nov 09 04:22:06 p21 systemd[1]: Starting WireGuard via wg-quick(8) for wg0...
Nov 09 04:22:06 p21 wg-quick[799]: [#] ip link add wg0 type wireguard
Nov 09 04:22:07 p21 wg-quick[799]: [#] wg setconf wg0 /dev/fd/63
Nov 09 04:22:07 p21 wg-quick[799]: [#] ip -4 address add 192.168.128.7/32 dev w>
Nov 09 04:22:07 p21 wg-quick[799]: [#] ip link set mtu 1420 up dev wg0
Nov 09 04:22:07 p21 wg-quick[799]: [#] ip -4 route add 192.168.128.0/24 dev wg0
Nov 09 04:22:07 p21 systemd[1]: Started WireGuard via wg-quick(8) for wg0.
[tuyendq@p21 ~]$ sudo systemctl enable wg-quick@wg0
Created symlink /etc/systemd/system/multi-user.target.wants/wg-quick@wg0.service → /usr/lib/systemd/system/wg-quick@.service.
[tuyendq@p21 ~]$
Wireguard on Raspberry Pi 2 Model B Rev 1.1 running Raspbian GNU/Linux 10 (buster)
pi@pi21:~ $ hostnamectl
Static hostname: pi21
Icon name: computer
Machine ID: 80fbdf8633694b66a65671a29ad4b2a9
Boot ID: 0c323c42b3eb4713a9c895ff8b0f9eb1
Operating System: Raspbian GNU/Linux 10 (buster)
Kernel: Linux 4.19.97-v7+
Architecture: arm
sudo apt-get install raspberrypi-kernel-headers libmnl-dev libelf-dev build-essential git
pi@pi21:~ $ git clone https://git.zx2c4.com/WireGuard Cloning into 'WireGuard'... warning: redirecting to https://git.zx2c4.com/wireguard-monolithic-historical/ remote: Enumerating objects: 17, done. remote: Counting objects: 100% (17/17), done. remote: Compressing objects: 100% (17/17), done. remote: Total 11550 (delta 0), reused 0 (delta 0), pack-reused 11533 Receiving objects: 100% (11550/11550), 2.39 MiB | 775.00 KiB/s, done. Resolving deltas: 100% (8638/8638), done. pi@pi21:~ $ cd WireGuard/src/ pi@pi21:~/WireGuard/src $ make pi@pi21:~/WireGuard/src $ sudo make install pi@pi21:~/WireGuard/src $ which wg /usr/bin/wg pi@pi21:~/WireGuard/src $
Wireguard on Oracle Linux
[opc@ol1 ~]$ sudo yum install -y wireguard-dkms wireguard-tools